CSAW 23 Philanthropy
Philanthropy was one of the "web" challenges presented in the CSAW 23 CTF challenge.
Summary
Philanthropy was a Metal Gear Solid themed web application hosted at web.csaw.io:14180. The application suffered from an improper API authentication vulnerability that allowed for user privilege escalation to "member" status.
Once escalated to "member", the application endpoint /verify/images suffered from a broken authentication vulnerability that permitted incorrect users to view confidential information belonging to other users on the site.
Using information gained in this manner, sufficient information existed to compromise a high-privilege account, which lead to the exfiltration of the challenge's flag.
Service Enumeration
As this was a web-specific challenge, full external service enumeration was not undertaken. Instead, scope was limited to http://web.csaw.io:14180/*, and so only web enumeration methodologies were applied.
An initial brute force scan of the sites endpoints was attempted using FFUF, however, this yielded no actionable results; all wordlist items returned 200, likely indicating that there was some sort of security measure preventing scanning.
From here, manual enumeration was attempted.
Endpoint /web/login presented a basic login prompt for username and password. Basic SQLi and OS command injection was attempted through these fields, but resulted in nothing.
Endpoint /web/register permitted public registration of new accounts. An account was created using the email address a@a.a and a password of a. Note that this indicates that this organization hypothetically has no password length or complexity policy, which could be an issue were this a real organization.
Once authenticated as our newly created account, endpoint /web/membership became available. This page contained a single text input prompting for a membership upgrade code. This field was similarly tested for SQLi and OS command injection, which again resulted in no vulnerabilities being discovered.
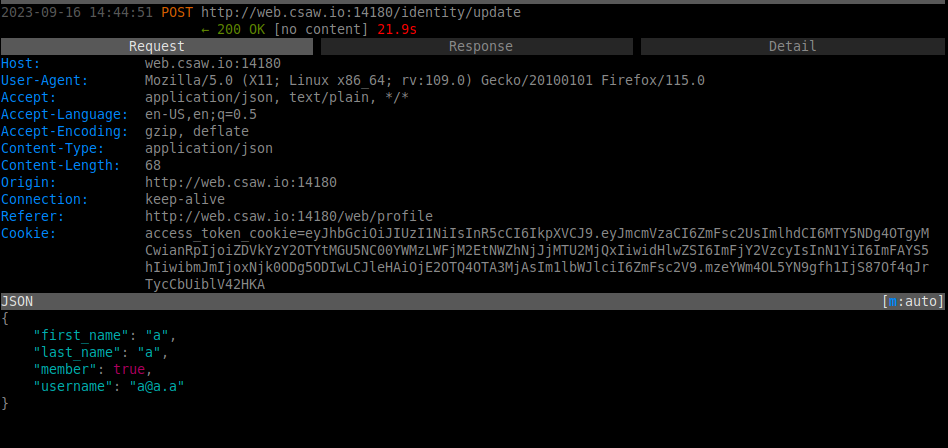
Endpoint /web/profile also became available once authenticated, which was a panel permitting the user to update account information. When actually performing updates, the application sends a POST request to the endpoint /identity/update, which receives input via JSON containing several, including the user's membership status.
This API endpoint does not require authentication beyond simple user level in order to make updates, and by permitting the user to update their membership status, appears to be a vulnerability that allows an attacker to elevate their privileges.
Vulnerability Explanation
Improper API Authentication.
By allowing unprivileged accounts to have access to an API that can alter an account's privilege level, this allows for attackers to arbitrary elevate their privileges within the application.
Vulnerability Fix
- Please consider ensuring that the "Membership" object on the API endpoint
/identity/updatecan only be written to by authorized parties.
Severity
Assessed CVSS: 5.4 medium
Proof Of Concept Code
Image of modified header demonstrating an authenticated but low privilege account setting their membership status to "true":
Privilege Escalation
Once member privileges were obtained, further endpoints became available, one of which was /web/flag, however attempting to access this endpoint resulted in a message claiming the user is unauthorized.
Another endpoint was a "game" presenting several images from the video game series "Metal Gear Solid" asking the user to identify whether various images depicted a "Metal Gear" or not.
The images were served via endpoint /verify/images, which during the course of the game took the parameter ?user=%22otacon@protonmail.com%22
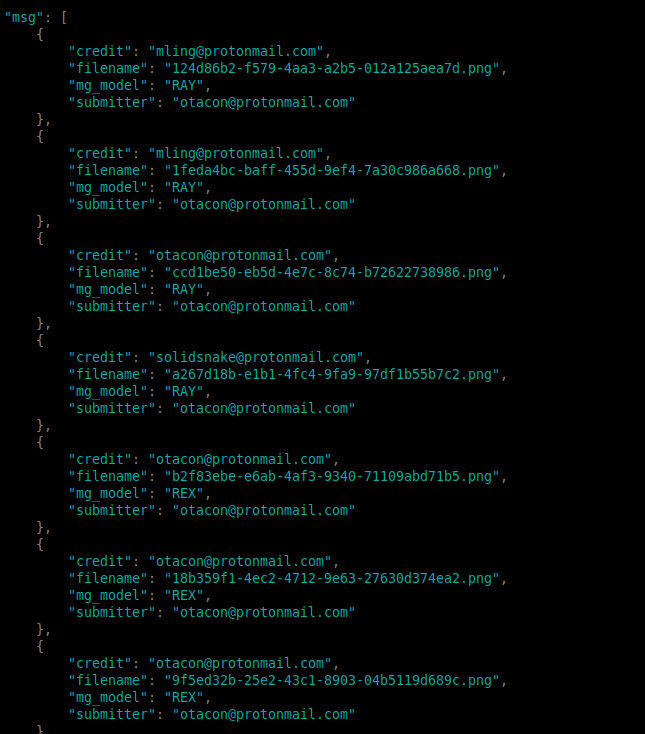
This page presented the following:
This information provided a list of email accounts for the users which supposedly submitted the various images displayed through the Metal Gear Game.
Going from the fact that "Solid Snake" is the protagonist of the Metal Gear Solid series that this challenge was themed around, the revealed address solidsnake@protonmail.com was injected into the parameter on /verify/images in order to test for a broken authentication vulnerability with what could be expected to be a high privilege account's credential.
This caused the endpoint to output data that was seemingly confidential to the solidsnake@protonmail.com user; namely, the account's credentials for the site.
These credentials were then utilized to login as the Solid Snake user, who's account was authorized to view the /web/flag endpoint.
Vulnerability Explanation
Broken authentication.
By allowing the application to access information confidential to each user account without validating either the login session ID or the necessary credentials, an attacker is able to exfiltrate confidential information without proper authorization.
Vulnerability Fix
- Please consider ensuring that
/verify/imagesvalidates the logon session of the user against the?userparameter's contents in order to ensure that users are only able to access their own content.
Severity
Assessed CVSS 3.0: 7.7 high.
Proof Of Concept Code
Header used to exploit "solid snake" broken authentication on /verify/images:
GET /identity/images?user=%22solidsnake@protonmail.com%22 HTTP/1.1
Host: web.csaw.io:14180
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Referer: http://web.csaw.io:14180/web/identify
Cookie: access_token_cookie=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTY5NDkwNzc2NCwianRpIjoiNGNkYWY5MzgtOTljYS00OGQ3LWJiMTYtMTY3OTgyY2UzMGEwIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImEiLCJuYmYiOjE2OTQ5MDc3NjQsImV4cCI6MTY5NDkwODY2NCwibWVtYmVyIjpmYWxzZX0.fDEEQ0wlv4Xd8niln7PCuwBahGEAoZwo_LkJw8KNVII
Proof Screenshot
Proof Text
csawctf{K3pt_y0u_Wa1t1ng_HUh}